Logical topology :
the mapping of the flow of data between the nodes in the network determines the logical topology of the network
Physical topology
Any given node in the LAN will have one or more links to one or more other nodes in the network and the mapping of these links and nodes onto a graph results in a geometrical shape that determines the physical topology of the network
There are several basic types of topology in networks:
1. Bus topology
A linear bus topology consists of a main run of cable with a terminator at each end. All nodes (file server, workstations, and peripherals) are connected to the linear cable.Ethernet and LocalTalk networks use a linear bus topology.The bus cable carries the transmitted message along the cable. As the message arrives at each workstation, the workstation computer checks the destination address contained in the message to see if it matches it's own. If the address does not match, the workstation does nothing more. If the workstation address matches that contained in the message, the workstation processes the message. The message is transmitted along the cable and is visible to all computers connected to that cable.
Advantages of a Linear Bus Topology
- Easy to connect a computer or peripheral to a linear bus.
- Requires less cable length than a star topology.
- Entire network shuts down if there is a break in the main cable.
- A faulty cable or workstation will take the entire LAN down
- terminators are required at both ends of the backbone cable.
- Difficult to identify the problem if the entire network shuts down.
- Not meant to be used as a stand-alone solution in a large building.
2.Star topology
A star topology is designed with each node (file server, workstations, and peripherals) connected directly to a central network hub or concentrator. Data on a star network passes through the hub or concentrator before continuing to its destination. The hub or concentrator manages and controls all functions of the network. It also acts as a repeater for the data flow.This configuration is common with twisted pair cable; however, it can also be used with coaxial cable or fiber optic cable.The protocols used with star configurations are usually Ethernet or LocalTalk.
Advantages
- Easy to install, and wire.
- Easy to add new workstations
- No disruptions to the network when connecting or removing devices.
- Any non-centralised failure will have very little effect on the network
- Easy to detect faults and to remove parts.
- Centralized control Centralized network/hub monitoring
Disadvantages
- Requires more cable length than a linear topology.
- If the hub or concentrator fails, nodes attached are disabled.
- More expensive than linear bus topologies because of the cost of the concentrators.
A star-wired topology may appear (externally) to be the same as a star topology. Internally, the MAU (multistation access unit) of a star-wired ring contains wiring that allows information to pass from one device to another in a circle or ring. The Token Ring protocol uses a star-wired topology.
4.
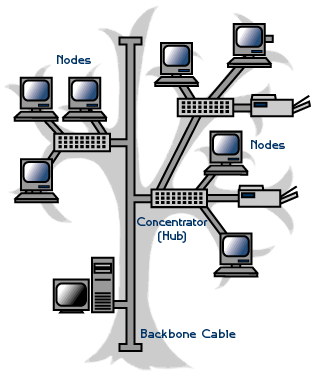
tree topology
A tree topology combines characteristics of linear bus and star topologies.It consists of groups of star-configured workstations connected to a linear bus backbone cable. Tree topologies allow for the expansion of an existing network, and enable schools to configure a network to meet their needs.
A tree topology combines characteristics of linear bus and star topologies.It consists of groups of star-configured workstations connected to a linear bus backbone cable. Tree topologies allow for the expansion of an existing network, and enable schools to configure a network to meet their needs.
Advantage
- Point-to-point wiring for individual segments.
- Overall length of each segment is limited by the type of cabling used.
- if the backbone line breaks, the entire segment goes down.
- More difficult to configure and wire than other topologies.
VIDEO!!!
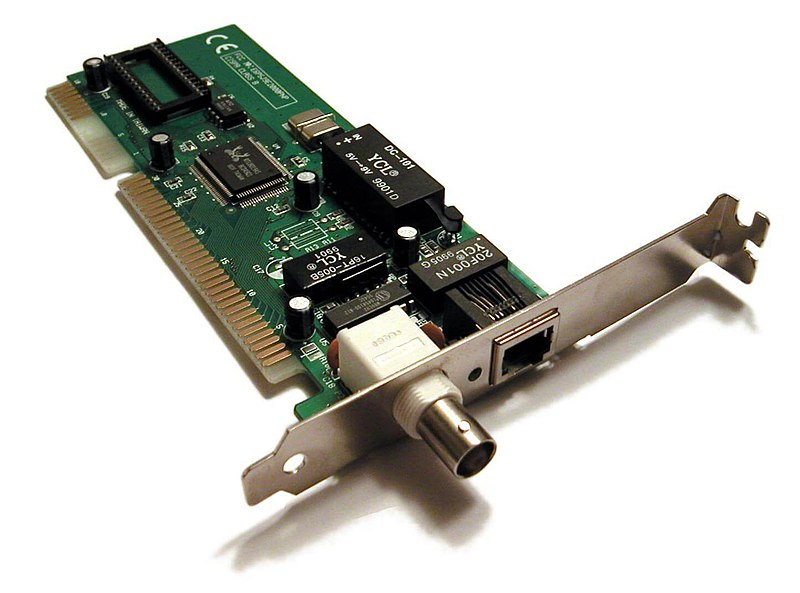
1. A network interface controller is a computer hardware component that connects a computer to a computer network.Whereas network interface controllers were commonly implemented on expansion cards that plug into a computer bus, the low cost and ubiquity of the Ethernet standard means that most newer computers have a network interface built into the motherboard.
2. A networking operating system (NOS) is the software that runs on a server and enables the server to manage data, users, groups, security, applications, and other networking functions. The network operating system is designed to allow shared file and printer access among multiple computers in a network, typically a local area network (LAN), a private network or to other networks. The most popular network operating systems are Microsoft Windows Server 2003, Microsoft Windows Server 2008, UNIX,Linux, Mac OS X, and Novell NetWare.
3. A network switch or switching hub is a computer networking device that connects network devices. The term commonly refers to a multi-port network bridge that processes and routes data at the data link layer of the OSI model. Switches that additionally process data at the network layer and above are often referred to as layer-3 switches or multilayer switches.
4. REPEATER is a network device used to regenerate or replicate a signal. Repeaters are used in transmission systems to regenerate analog or digital signals distorted by transmission loss. Analog repeaters frequently can only amplify the signal while digital repeaters can reconstruct a signal to near its original quality. In a data network, a repeater can relay messages between sub networks that use different protocols or cable types. Hubs can operate as repeaters by relaying messages to all connected computers. A repeater cannot do the intelligent routing performed by bridges and routers.
5. LocalTalk refers to the physical networking -- that means the built-in controller in many Apple computers, the cables and the expansion cards required on some systems. The "official" Apple cabling system typically uses a "bus topology" where each device in the network is directly connected to the next device in a daisy chain. The illustration on the Farallon book cover below gives an idea of how a bus looks.
6. Token ring local area network (LAN) technology is a local area network protocol which resides at the data link layer (DLL) of the OSI model. It uses a special three-byte frame called a token that travels around the ring. Token-possession grants the possessor permission to transmit on the medium. Token ring frames travel completely around the loop.
7. Ethernet is a family of computer networking technologies for local area networks (LANs) commercially introduced in 1980. Ethernet has largely replaced competing wired LAN technologies.
FOR THE FURTHER INFORMATION, PLZ CLICK: